Torrent Cracking 4 Way Handshake
There is a new version of this article., we showed you how to secure your wireless with industrial strength RADIUS authentication via WPA-Enterprise. It turns out that there's a little back-story there. So, in traditional Tarentino fashion, now that we've already seen the ending, let's back up to the beginning: cracking WPA-PSK. Wi-Fi Protected Access () was created to solve the gaping security flaws that plagued WEP. Perhaps the most predominant flaw in WEP is that the key is not hashed, but concatenated to the IV, allowing completely passive compromise of the network.
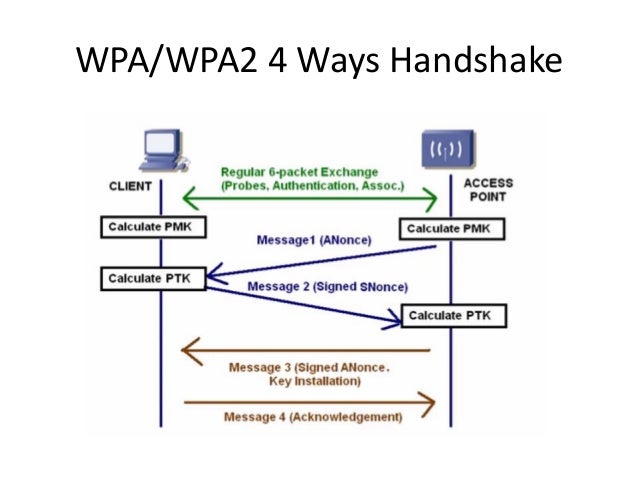

With WEP, you can literally sit in your car listening for packets on a network. Once you have captured enough of them, you can extract the key and connect to the network. WPA solves this problem by rotating the key on a per-packet basis, which renders the above method useless. However, nothing is perfectly secure, and WPA-PSK is particularly vulnerable during client association, during which the hashed network key is exchanged and validated in a 'four-way handshake'.
Short answer is, 4-way handshake password 'cracking' works by checking MIC in the 4th frame. That is, it only checks that KCK part of the PTK is correct. Here we will automatically select best suited wordlists and keyspaces to maximize your chances to win the lottery. Advanced WPA search usually takes 1-3 hours. Fastest Way Of WPA/WPA2 Cracking. Then we’ll deauthenticate a target and when it reauthenticates we’ll have our capture file of the 4 way handshake.
The Wi-Fi Alliance, creators of WPA, were aware of this vulnerability and took precautions accordingly. Instead of concatenating the key in the IV (the weakness of WEP), WPA hashes they key using the wireless access point's SSID as a salt. The benefits of this are two-fold. First, this prevents the statistical key grabbing techniques that broke WEP by transmitting the key as a hash (cyphertext). It also makes hash precomputation via a technique similar to more difficult because the SSID is used as a salt for the hash.
WPA-PSK even imposes a eight character minimum on PSK passphrases, making bruteforce attacks less feasible. So, like virtually all security modalities, the weakness comes down to the passphrase. WPA-PSK is particularly susceptible to dictionary attacks against weak passphrases. In this How To, we'll show you how to crack weak WPA-PSK implementations and give you some tips for setting up a secure WPA-PSK AP for your SOHO.
I was messing around in my lab last night and - (think) I found a really easy way to get a WPA handshake. However, I want to run this by everyone and see if I am way off base here. So I had an airodunmp-ng running capturing packets - trying to find way to get a handshake if no clients were available to deauth - so I had a brand new phone - that's never been connected to my lab network before. I enabled Wifi on my new phone and tried to connect to my labs AP - I used the wrong PIN/Pass Phrase on purpose - my phone stated it was the wrong PIN/Pass Phrase - however I noticed that I got a WPA Handshake. I was able to reproduce this over and over again. Has anyone else seen this?
Is this normal? My understanding to get an successful WPA Handshake - you need a client to connect successfully to the AP. **Note I haven't tried to crack the.cap file yet.
My lab is just using an older Linksys wireless-g router. Tested this on a 2wire AT&T one - worked as well.
I will try to process the cap file tonight. I've never used CoWPAtty - so I will find the command and switches to try and process it with that as well. (If aircrack does not work) Was anyone else able replicate this? This would beat having to deauth or wait for someone to connect. Digininja - thanks for the script -:) been working on a FakeAP + Metaspolit one - just trying to teach myself basic scripting (coming from a strict VBscript background).